Elevate your field service operations with an enterprise-grade platform
Keep pace with your security and compliance standards
Large-scale enterprises have clear policies and strict guidelines on IT and how it’s used within the organization.
east
Broaden your field capabilities with a solution that does the job without sacrificing security or compliance.
Rules exist to ensure data security, maintain regulatory compliance, and prevent the incidence of shadow IT that can expose the business to significant risk. Highly regulated operations must meet even higher standards before any new technology can be integrated into their infrastructure.
As a result, however, field leaders often encounter roadblocks in adding software that may be critical to the work they do, complicating an otherwise simple extension.
In step with your compliance requirements
Enterprises often deal with sensitive customer data with specific policies set by industry regulators. TrueContext maintains compliance with these frameworks on an ongoing basis so customers can integrate our solution into their IT systems with confidence.

HIPAA
TrueContext is third-party-verified for the HIPAA Security Rule and HITECH act to ensure all electronic health information is protected.

SOC 2 Type II
Internal controls for security, confidentiality, and availability of customer data within the platform are regularly evaluated and certified.

FDA
A Title 21 CFR Part 11 seal guarantees the validity, security, and audit visibility of electronic records and electronic signatures.
Getting security right is important to TrueContext, so we are constantly striving to maintain and improve our security program. TrueContext subscribes to news and updates from industry leaders in security and vulnerability management, which equips us to stay ahead of any risks. Don’t just take our word for it, we take on regular audits to verify our security and privacy practices and operations.
Auditor attestations available upon request.
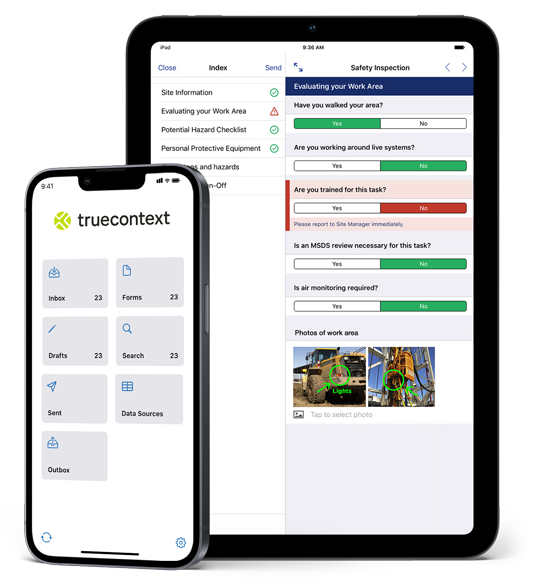
A platform that values data as much as you do
Over 99.9% system availability
Data-on-demand is the cornerstone of a modern, digital-first organization. Interruptions of any kind or duration can create blind spots in decision-making other critical business functions. TrueContext maintains over 99.9% data availability by using safeguards that detect and address system performance issues, with a team of on-call support staff ready to respond to and resolve incidents. Incident response and disaster recovery plans are routinely rehearsed and evaluated to stay ahead of the ever-evolving security landscape.
Cutting-edge security
Our solution uses TLS 1.2 encryption for data in transit and AES 256 at rest to ensure that customer data is always protected. TrueContext developers receive regular training in secure coding practices, and all code is rigorously examined for vulnerabilities prior to each release. Third-party penetration testing and resolution is also a crucial part of the development process, resulting in an app with bulletproof security.
Easy to deploy, even easier to manage
Integrate TrueContext with optimized native performance no matter what platform your teams are on. The app works with iOS, macOS, Android, and Windows mobile devices and can be managed easily through existing MDM solutions or directly through your app stores.
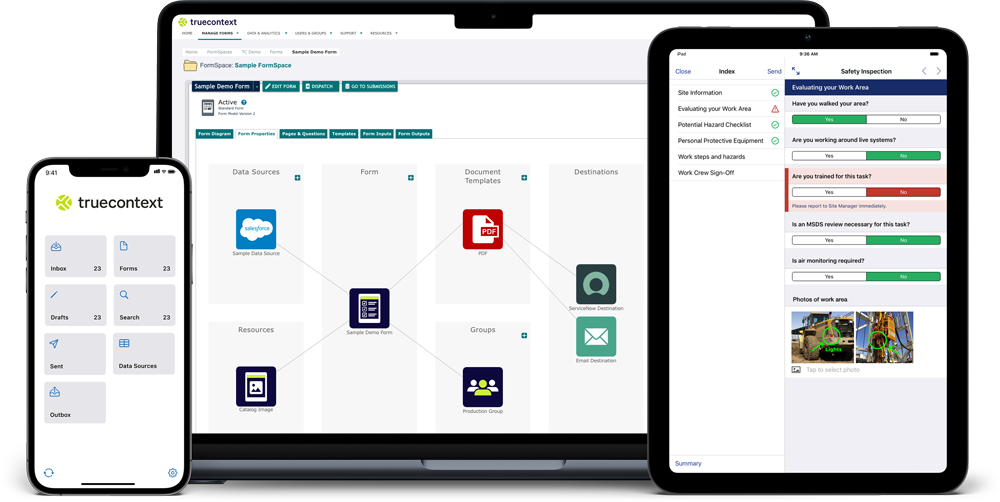
Process-oriented safeguards
Technology-driven security standards can only go so far if the underlying procedures are not up to the task. How customer data is handled is an equally important part of the equation and our processes support this.
Data and access management
Data can be stored on TrueContext servers or a preferred destination. The platform is also compatible with many identity management protocols (EMM, SSO, etc.) Our platform also allows you to set password complexity policies for your users. Passwords are hashed and salted so no one can gain unauthorized access.
Internal security
Internally, TrueContext staff must pass a background check and complete monthly security training. The principle of least privilege applies to the entire organization – only those who need it have access to sensitive systems and data. These systems are carefully monitored to keep our customers’ data secure.

Its integration with our CRM tools in our offices make it very easy to keep track of all details of our customers. On data security, this tool prevent other unauthorised parties from accessing our sensitive data through data encryption.
MYLAR A.
SYSTEMS MANAGER
This tool is highly secure and easy to scale. I like how this tool meets compliance requirements by reducing compliance risks/incidence.
Brianna W.
Software Engineer
We can smoothly import and export data thanks to the integrations with software like Salesforce and Dropbox.
Grant B.
Account Director

Frequently Asked Questions
How does TrueContext keep my data secure?
How is my data secured on hosted systems in the cloud?
Is my data also secured on iOS and Android mobile devices?
Can I access TrueContext via single sign-on (SSO)?
Has TrueContext achieved SOC 2 compliance?
What’s the difference between SOC 2 Type II and other compliance certifications (such as ISO)?
Is TrueContext HIPAA Security Rule and HITECH Act compliant?
Can TrueContext’s employees simply view the data in our TrueContext account?
Does TrueContext screen employees prior to hiring?
Do TrueContext employees adhere to secure coding guidelines?
Does TrueContext sign data processing agreements?
Does TrueContext have 24/7 security incident management capabilities?
Does TrueContext have a disaster recovery strategy?
What steps has TrueContext taken to proactively mitigate Distributed Denial of Service (DDOS) attacks and other malicious attacks?
Does TrueContext offer any specific technology for customers who provide regulated services, such as those in the medical field?
Have questions about data security? Ask our experts.
We're always happy to answer any questions or concerns you might have around security.
Reports and agreements are available to existing customers upon request to infosec@truecontext.com.